Some time ago I blogged about the first release of NiCE Log File Library, you find the post here . I was very excited that NiCE released a free MP which provides lots of rules and monitors that can be configured in countless ways. It provide many capabilities to monitor any kind of log files on a Windows system. The good news is that NiCE released a new improved version of their Log File Library Version 1.30.
So what’s new?
- Improved SCOM Authoring Console Wizards
- Improved Cluster Support
- Fixing some minor cluster issues
- Self-Monitoring enhanced
- Several rules to monitor the MP itself and discovering configuration issues.
- Performance and stability improvements
Features & Functionalities of the NiCE Log File MP
- Equipped with a set of custom authoring wizards so you can create
- Alert Rules
- Performance Counters
- Unit Monitors
- Allows you to filter log entries using regular expression language
- Includes a powerful program execution interface to run scripts and programs
- Correlate your log lines
- Allows you to define log file names as absolute paths
- Customize behavior if log file does not exist
- Set the log file directory using a regex pattern with no restriction
The in-place upgrade from version 1.27 is supported and the new installation itself runs without any issue. NiCE provides a solid MP which rocks like hell (FOR FREE) but what could be a NiCE use case?
I have seen some questions in the TechNet forums how to create a SCOM alert from mail. I think this is a perfect use case for this MP. Ok, let’s assume we would not have this MP how would we create a SCOM alert from mail? E.g you could use Orchestrator or SMA to connect to an Exchange or other mailbox and query / pull for the mail using Orchestrator IP or PowerShell. This is a valid solution, but I think there are too many systems involved and maybe not everyone has the necessary skills or systems to do it. I would suggest to try an other approach, like using the Windows built-in SMTP service to receive the mails and the NiCE MP to parse the mails and create an appropriate alert.
Install SMTP Server
For ease of use I installed the SMTP service on my SCOM server OM01. Go to the “Add Roles and Features Wizard” and select “SMTP Server”…
“Add Features”…
…and hit “Install”….
Configure SMTP Server
Open the IIS 6.0 Manager and select “Properties”…
Assign the IP address of the server to the server…
Depending on your needs you might need to enable all authentication methods on the “Access” tab like here…
In order to relay itself you need to add the server’s (OM01) loopback and IP address to the “Relay Restriction” tab. Depending on your situation you might need to add other relay access rules…
The rest of the SMTP server settings are not needed to change for this example. Of course in production you would need to make sure that all other settings fit your company policies.
What happen, when you try to send a mail to this SMTP server? The server will accept your mail and put it into the default C:\inetpub\mailroot\Queue folder, because it cannot be sent to another mail server…
Later on I’ll show you how to test it.
Installing the NiCE Log File Library
Download the package from NiCE.de and run the installer NiCE_LogFileMP_0130.msi to extract the MPB file. There is just one management pack bundle file which you need to import, if you are installing the MP for the first time, just import it or you could upgrade it from a previous version 1.27. The prerequisites are minimal just make sure .NET 2.0 SP1 is already installed on all systems that are monitored.
Create Alert Rule
Go to Authoring in SCOM and select Rules and start the wizard. Select “Expression Filtered / Alert Rule (Advanced)”…
Click “Next” and give the rule a name, choose the target and disable the rule…
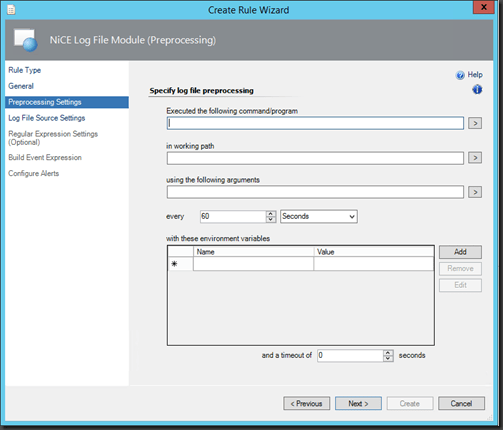
Click “Next” , on this page you could run a command which would e.g. in out scenario delete old mails from the directory before the rule actually runs…
Click “Next” and select the log file path and a name pattern for the mails. The mails start with “NTFS_” and end with “.EML”.
“Next” and enter the optional expression “Subject:” to find filter the log file entries. In order to split the log file in different parts use this expression:
Subject:\s+(?<Severity>\w+)\s+(?<Device>\w+)\s+(?<Location>\w+)
Using this expression, splits the line in “named” groups which can be used to refer e.g. in the alert description. I have three different parts “Severity” (e.g. Critical), “Device” (name of the device) and “Location” (location of the device RZ1, Datacenter1 etc.). Click “Regex testing tool”…
Using the built-in “Regex testing tool” helps you to check your expressions. Under “Logfile Line” enter the subject line you want to send by mail. In my example I just use spaces (\s+) to separate the information. The “Sample Output (XML)” shows you what the actual output is and if your expression works…
On the other tab “XPath” see the available variable you could use in the event filtering or alert description…
Click “Ok” and “Next”, on the next page setup the event filtering, here I will receive an alert if severity is “Critical” and the device is “Router01” in the subject line…
Click “Next” and enter the alert name and description. In my case I use the variables from before and refer to it like this…
The Router $Data/RegexMatch/Device$ in $Data/RegexMatch/Location$ sent a critical alert received by mail.
The mail is $Data/LogFileName$.
Next override the rule for just the object, where you have the SMTP service installed, in my case OM01. Choose “For a specific object of class Windows Server 2012 Operating System”, in my case the OM01, where the rule will be run…
Set “Enable” to “True”….
That’s it, everything is now configured to test the rule.
Create Mail
We have configured the SMTP service to receive mails from OM01. Because I don’t have a router or anything like that available to generate a mail I use PowerShell. PowerShell has a cmdlet Send-MailMessage which perfectly fits our needs. To fire a mail we type the following command…
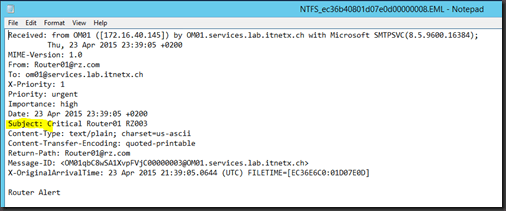
Send-MailMessage -Body “Router Alert” -From “Router01@rz.com” -SmtpServer 172.16.40.145 -Priority High -Subject “Critical Router01 RZ003” -To om01@services.lab.itnetx.ch
If this command succeeds you will find the mail in the queued directory of the SMTP server…
…and will look like this…
In my lab it took about 5-6 min for the rule to pick up the mail and parse it and finally creating the alert…
Of course you could configure any device to send a mail to the SMTP server and generating an alert. I have not tested it in a production environment how everything would behave, however I think it is a cool idea and a good starting point if you need such an approach. You could improve performance, by frequently deleting the “old” mails from the “Queue directory” e.g. by using the “Preprocessing Settings” of this rule.
There are many more rules to explore of the NiCE Log File Library, so make sure to download your copy today.





















Hi Stefan,
Thanks for this article: https://www.stefanroth.net/2015/04/20/scom-2012-nice-log-file-library-creating-alert-from-mail/.
I have tried this and have successfully configured SMTP and tested queuing the .EML file.
Even though I have followed your blog every step of the way, I haven’t been able to get my SCOM to pick up the queued E-Mail and its content.
I have exactly replicated your example but nothing is being picked up.
Have create Rule and targeted my Test SMTP server as specified above and went over the settings 2 to 3 times but no success.
Can you please provide me some assistance on troubleshooting this?
Regards
Saiyad